May 20, 2013
Top 5 Server and Admin Applications for Android and iPhone
 No matter what is the nature of your work, whether you are a webmaster, server administrator or an IT professional, the ability is to deal with your admin tasks and the server is your utmost priority. In this article, we are going to discuss the top five server and admin applications that is suitable to your iPhone, and Android mobile gadgets.
No matter what is the nature of your work, whether you are a webmaster, server administrator or an IT professional, the ability is to deal with your admin tasks and the server is your utmost priority. In this article, we are going to discuss the top five server and admin applications that is suitable to your iPhone, and Android mobile gadgets.
1. AndFTP
For those who are not yet familiar about AndFTP it serves as an SCP, FTP, and SFTP and FTPS client. Moreover, AndFTP let the user to handle number of FTP configurations; as well it provides features like download and upload and sharing management. As well AndFTP allows the user to delete, rename, open, or update permissions, and also to run custom commands.
2. ConnectBot
ConnectBot act as a Secure Shell client intended for Android users, as well it creates secure connection through using a shell even the gadget is in the remote distance to transmit files and data back and forth to your phone. Furthermore, ConnectBot let the user to handle numbers of SSH sessions, as well allow them to copy and paste between other applications, and to build protected tunnels.
Jack Wallen an award winning writer of Linux.com stated that ConnectBot is a must have app, in fact he recommend this app to the Linux admin who are using Android phone.
3. ServerMonitor
ServerMonitor is an app intended for iPhone users, it uses SSH protocol to link machines remotely to assists with your workstation and server monitoring requirements. The multi-protocol supports include the following: FTP, SMTP, HTTP, IMAP, MySQL, HTTPS, DNS, POP3, Ping and SSH.
Although there is no much review regarding this app but the general response seems to be optimistic. Based on the feedback from the users one thing they want to be added in this app on the next update is the ability to view all list of running processes and to view how much memory they occupy.
4. iSSH – SSH / VNC Console
The iSSH – SSH / VNC Console for iPhone is an SSH and Telnet emulator that is fully featured with ANSI, VT102, VT100, and VT220 incorporated with tunneled X server, RDP client and VNC client. As well this app has the ability to carry simultaneous connections with total terminal compatibility, intuitive user interface, and configurable macro and key options.
5. Network Utility
Network Utility let the user to check the status of their server or websites through their Apple device or iPhone anywhere. Network Utility is fully featured with TCP/IP Port Scan, ping (ICMP Echo), IP address information, Whois Query, GeoIP Lookup, and more.
For me this another iPhone app that seems to be gathering mixed reviews. Some user approved its efficiency and its user friendliness, but other user rising complaint that this app causes their device to freeze up that can only be fixed through restarting the device. Users as well object about the absence of subnet scans. The decision is still out on this app. But the best thing we need to do is to try this and experience how it holds up.
About the Author:
Stacy Carter is a tech writer and freelance blogger laying out for tech news via online exposures. She is the author of the site: iPhone Spy where you can get valuable information about spy software program on your cell phone.
Author: dfgdfg,
April 4, 2013
Google plans to start sales of second-gen Nexus 7 tablet from July
Google Inc will launch a new version of its Nexus 7 tablet powered by Qualcomm Inc's Snapdragon processor around July, as the software giant pushes deeper into the cut-price mobile hardware market.
Google is aiming to ship as many as eight million of the Asustek-made tablets in the second half of the year, throwing down the gauntlet to other low-end tablets such as Amazon.com Inc's Kindle Fire and Apple Inc's iPad mini, the sources with knowledge of the new product said.
This is the first time details about the timing and sales targets for Google's new tablet have been unveiled, although the company has not publicly released any information.
Google, which gets almost all of its revenue from online advertising, wants the aggressively priced Nexus tablets to be a hit as more Nexus users would mean more exposure for Google's ads.
The latest version will have a higher screen resolution, a thinner bezel design and adopt Qualcomm's chip in place of Nvidia Corp's Tegra 3, which was used in the first Nexus 7s released last year, the sources said, declining to be identified because they are not authorized to speak to the media.
In a blow to Nvidia, Google weighed both U.S. chipmakers' processors but finally decided on Qualcomm's for power reasons, one of the sources added.
Qualcomm and Nvidia are competing aggressively in the tablet market as they seek to expand from their traditional strongholds of cellphones and PCs respectively.
A Google spokesman declined to comment on its new tablet. Qualcomm and Nvidia also declined to respond to questions.
Google and other traditionally non-hardware companies like Amazon and Microsoft Corp have begun making inroads into mobile devices as consumers increasingly access the Web on the go.
Google introduced its first tablet last June, hoping to replicate its smartphone success in a hotly contested market now dominated by Kindle Fire and iPad.
The Nexus 7 joined the ranks of smaller, 7-inch tablets popularized by Amazon and Samsung Electronics, among others.
Pricing is yet to be determined and Google's plans are fluid, the sources said. Market leader Apple is expected to launch new iPads this year as well, possibly forcing its competitors to change their assumptions.
Google may choose to sell the new gadget for $199, the same as the first generation rolled out last June, while the old model may be discounted, one of the sources said. Alternatively, the new tablet could be priced more competitively at $149 and the previous model discontinued, the source added.
The cheapest iPad mini goes for more than $300.
CORE STRENGTHS
Though pricing has not been finalized, discounting could play to Google's and Amazon's strengths by getting cheaper hardware into more consumers' hands to drive revenue from their core Internet-based businesses.
"This is the 'zero margin strategy'," said Fubon Securities analyst Arthur Liao. "Ninety-seven percent of Google's revenue comes from advertisement, so it needs to sell more mobile devices in order to reach more consumers."
The Internet search giant, which has never disclosed tablet sales, plans to ship six to eight million of the new Nexus 7s in the second half of this year, the sources said. That compares to an estimated 4.6 million Nexus 7s sold in the same period last year, according to Enders Analysis mobile industry analyst Benedict Evans.
The large volume could help to accelerate development of tablet-specific applications for its Android operating software.
Asustek, a netbook PC pioneer, will continue to co-brand with Google on the new Nexus 7. The Taiwanese company has said it aims to ship over 12 million tablets this year, almost double last year's shipments.
Author: dfgdfg,
April 2, 2013
11 Security Holes Addressed by Google in Chrome 26
Chrome 26 is officially out and, as always, the latest stable channel update comes with a number of improvements in the security section. However, on this occasion, only 2 high-severity vulnerabilities have been addressed.
One of the high-severity flaws has been uncovered by Atte Kettunen of OUSPG. The expert has been rewarded with $1,000 (780 EUR) for a use-after-free issue in Web Audio.
By fixing the other high-severity bug, Google ensures that isolated websites run in their own processes.
Of the four medium-severity vulnerabilities, one – a use-after-free with pop-up windows in extensions – affects only the Linux variant.
Five low-severity bugs have also been identified.
Most of the issues have been found by the Google Chrome Security Team and members of the Chromium development community.
Subho Halder, Aditya Gupta, and Dev Kar, all three of xys3c, and “t3553r” have also been credited for finding security holes.
Author: dfgdfg,
ID Analytics Launches eCommerce Fraud Detection Solutions
Fraud detection solutions launched by ID AnalyticsID Analytics has launched a series of solutions designed to help online retailers in their fight against fraud, a problem that costs companies around $3.4 billion (2.6 billion EUR) a year.
The eCommerce suit offered by ID Analytics can be used not only to stop fraudulent transactions before any money or time is wasted, but it can also reduce the number of false positive results reported by automated fraud detection systems.
The solutions include Transaction Protector, a score card that can identify over 80% of fraud charge-back losses in the riskiest two percent of transactions; Transaction Advanced Intelligence, which provides real-time risk insight based on a series of attributes; and Transaction Takeover, which detects when an account is overtaken by a fraudster.
“Fraudsters are becoming increasingly sophisticated, and eCommerce retailers still encounter too many false positives when screening for potential fraud,” explained Aaron Kline, director of eCommerce at ID Analytics.
“ID Analytics partners with merchants to help them fight fraud while ensuring that no additional friction is introduced into the online customer experience.”
Author: dfgdfg,
Saudi Arabia Government Threatens to Ban Skype, WhatsApp and other VOIP Services
No, not the US this time, Saudi Arabia is the latest to join the anti-Skype brigade as it threatens to ban essentially all VoIP communications in the country unless those communications fall within the regulations.
Regulations that involve the government being allowed to snoop in on communications, which can't be done practically if the communications are encrypted.
While the government hasn't said exactly why these apps are being targeted, it did mention Skype, WhatsApp and Viber as falling outside the rules. All three are very popular VoIP services, the latter two mostly on mobile phones.
Saudi Arabia has a history of going against communication methods it can't control, it banned BlackBerry's built-in messaging service temporarily a few years ago over the use of encryption.
Author: dfgdfg,
March 27, 2013
The Biggest DDos Attack in History, Disrupts Global Internet

A massive 300Gbps was thrown against Spamhaus' website but the anti-spam organisation was able to recover from the attack and get its core services back up and running. CloudFlare, the content delivery firm hired by Spamhaus last week to guard against an earlier run of DDoS attacks, was also hit, forcing it into taking the highly unusual step of dropping London as a hub in its network - as a Twitter update by CloudFlare on Monday explained.
Our peering in London has been dropped due to a large attack. Modifying routes to avoid degradation.Affecting location: London, GB
— CloudFlareStatus (@CloudFlareSys) March 25, 2013
Spamhaus supplies lists of IP addresses for servers and computers on the net linked to the distribution of spam. The blacklists supplied by the not-for-profit organisation are used by ISPs, large corporations and spam filtering vendors to block the worst sources of junk mail before other spam filtering measures are brought into play.
Spammers, of course, hate this practice so it's no big surprise that Spamhaus gets threatened, sued, and DDoSed regularly. Those affected by what they regard as incorrect listings also object about Spamhaus' alleged vigilante tactics.
The latest run of attacks began on 18 March with a 10Gbps packet flood that saturated Spamhaus' connection to the rest of the Internet and knocked its site offline. Spamhaus's blocklists are distributed via DNS and widely mirrored in order to ensure that it is resilient to attacks. The website, however, was unreachable and the blacklists weren't getting updated.
The largest source of attack traffic against Spamhaus came from DNS reflection, launched through Open DNS resolvers rather than directly via compromised networks. Spamhaus turned to CloudFlare for help and the content delivery firm was able to mitigate attacks that reached a peak of 75Gbps, as explained in a blog post here.
Things remained calm for a few days before kicking off again with even greater intensity - to the extent that collateral damage was seen against services such as Netflix, the New York Times reports.
Spamhaus' site remains available at the time of writing on Wednesday. Steve Linford, chief executive for Spamhaus, told the BBC that the scale of the attack was unprecedented.
"We've been under this cyber-attack for well over a week.But we're up - they haven't been able to knock us down. Our engineers are doing an immense job in keeping it up - this sort of attack would take down pretty much anything else," he said.
Turning up the volume of DDoS attacks
A blog post by CloudFlare, written last week before the latest run of attacks, explains the mechanism of the attack against Spamhaus and how it can be usde to amplify packet floods.CloudFlare reckons 30,000 unique DNS resolvers have been involved in the attack against Spamhaus.
The basic technique of a DNS reflection attack is to send a request for a large DNS zone file with the source IP address spoofed to be the intended victim to a large number of open DNS resolvers. The resolvers then respond to the request, sending the large DNS zone answer to the intended victim. The attackers' requests themselves are only a fraction of the size of the responses, meaning the attacker can effectively amplify their attack to many times the size of the bandwidth resources they themselves control.
In the Spamhaus case, the attacker was sending requests for the DNS zone file for ripe.net to open DNS resolvers. The attacker spoofed the CloudFlare IPs we'd issued for Spamhaus as the source in their DNS requests. The open resolvers responded with DNS zone file, generating collectively approximately 75Gbps of attack traffic. The requests were likely approximately 36 bytes long (e.g. dig ANY ripe.net @X.X.X.X +edns=0 +bufsize=4096, where X.X.X.X is replaced with the IP address of an open DNS resolver) and the response was approximately 3,000 bytes, translating to a 100x amplification factor.
"Because the attacker used a DNS amplification, the attacker only needed to control a botnet or cluster of servers to generate 750Mbps - which is possible with a small sized botnet or a handful of AWS instances," it explains.
Author: dfgdfg,
March 22, 2013
Advance SystemCare Pro 6 Latest Version for 2013 License Key
 Advanced SystemCare PRO provides an always-on, automated, all-in-one PC Healthcare Service with anti-spyware, privacy protection, performance tune-ups, and system cleaning capabilities. This powerful and award-winning precision tool fixes stubborn errors, cleans out clutter, optimizes Internet and download speeds, ensures personal security, and maintains maximum computer performance automatically. Key benefits include:
Advanced SystemCare PRO provides an always-on, automated, all-in-one PC Healthcare Service with anti-spyware, privacy protection, performance tune-ups, and system cleaning capabilities. This powerful and award-winning precision tool fixes stubborn errors, cleans out clutter, optimizes Internet and download speeds, ensures personal security, and maintains maximum computer performance automatically. Key benefits include:
1) Keeps your PC running at peak performance: Fully optimizes Windows for ultimate system performance and top Internet speed by unleashing the built-in power of your system, based on how you use your PC and your network configuration.
2) It turns your PC into a business PC, a productive workstation, an entertainment center, a game machine, or a scientific computing PC.
3) Defends PC security with extra protection: Detects and analyzes Windows security environment. Scans and removes spyware and adware using up-to-date definition files. Prevents spyware, hackers and hijackers from installing malicious programs on your computer.
4) Erases and updates your PC's activity histories. One click to solve as many as 10 common PC problems: Advanced SystemCare 5 inherits the ease-of-use from previous versions, with more powerful capabilities. With one click, it scans and repairs ten PC problems and protects your PC from hidden security threats.
5) Real-time optimization with ActiveBoost function: ActiveBoost, technology that actively runs in the background intelligently managing system resources in real-time, constantly detecting inactive resources and optimizing CPU and RAM usage.
What’s New in Advanced SystemCare 6
- Brand New User Interface – The New One-Click Solution Provides Maximum Convenience to Conduct a Comprehensive PC-Care with Just a Click of a Button.
- New Web Surfing Protection – Creates a Safer Online Environment by Detecting Risky Websites and Other E-threats that May Harm Your PC.
- New Internet Boost Technology – Provides Smoother Online Experience by Accelerating Internet Downloading, Web Surfing, Online Video and Gaming up to 300% Faster.
- New Generation Disk Defragment Engine – Makes Disk Scanning and Optimization Much Faster by Intelligently Organizing Drive Data for Maximum Performance.
4A639-FD966-C5435-512C4 (4 months from now)
65792-57FC4-5CEC1-677C4 (not sure)
Author: dfgdfg,
March 19, 2013
AT&T Hacker Sentenced to 41 Months in Prison
 Andrew Auernheimer – aka “Weev,” the Internet activist found guilty in November 2012 of hacking into the systems of AT&T and stealing the details of around 120,000 iPad owners – has been reportedly sentenced to 41 months in prison and three years of supervised release.
Andrew Auernheimer – aka “Weev,” the Internet activist found guilty in November 2012 of hacking into the systems of AT&T and stealing the details of around 120,000 iPad owners – has been reportedly sentenced to 41 months in prison and three years of supervised release.Tweets are being posted from the courthouse where the trial is taking place.
Tim Pool of Timcast, who has been following the trial from the court, says Auernheimer and his co-defendant Daniel Spitler will also have to pay $73,000 (56,000 EUR) in restitution to AT&T.
“Judge stated the sentence she administered would help weev down a ‘positive path’ and give him ‘respect for the law’,” Pool wrote.
One noteworthy aspect is the fact that the prosecution apparently used Auernheimer's Reddit AMA (ask-me-anything) to justify the sentencing.
In addition, at one point in the trial, court agents asked Weev to hand over his phone. He gave the device to his lawyer instead, after which he was “quickly grabbed, pinned, and cuffed.”
Auernheimer maintained his innocence up until the last minute. He has highlighted on numerous occasions that he wasn’t trying to cause any harm.
His tweet just before the trial.
No matter what the outcome, I will not be broken. I am antifragile.
— Andrew Auernheimer (@rabite) March 18, 2013
Author: dfgdfg,
March 13, 2013
Download SSLyze v0.6 – SSL Server Configuration Scanning Tool
 SSLyze is a Python tool that can analyze the SSL configuration of a server by connecting to it. It is designed to be fast and comprehensive, and should help organizations and testers identify misconfigurations affecting their SSL servers.
SSLyze is a Python tool that can analyze the SSL configuration of a server by connecting to it. It is designed to be fast and comprehensive, and should help organizations and testers identify misconfigurations affecting their SSL servers.
Key features include:
- SSL 2.0/3.0 and TLS 1.0/1.1/1.2 compatibility
- Performance testing: session resumption and TLS tickets support
- Security testing: weak cipher suites, insecure renegation, CRIME and THC-SSL DOS attacks
- Server certificate validation
- Support for StartTLS with SMTP and XMPP, and traffic tunneling through an HTTPS proxy
- Client certificate support for servers performing mutual authentication
- Scan results can be written to an XML file for further processing
- Added support for Server Name Indication; see –sni
- Partial results are returned when the server requires client authentication but no client certificate was provided
- Preliminary IPv6 support
- Various bug fixes and better support of client authentication and HTTPS tunneling
Linux/OSX – sslyze-0.6_src.zip
Windows 7/Python 32-bit – sslyze-0.6_Windows7_Python32.zip
Windows 7/Python 64-bit – sslyze-0.6_Windows7_Python64.zip
Read more here.
Author: dfgdfg,
March 8, 2013
Pwn2Own ends with Oracle Java, Reader and Adobe Flash exploits
 Day two of the Pwn2Own competition at CanSecWest was again successful for French Vupen security, as they succeeded in exploiting Adobe Flash on Internet Explorer 9 on Windows 7 by chaining together three zero-days (an overflow, a ASLR bypass technique and a IE9 sandbox memory corruption) and earning themselves another $70,000.
Day two of the Pwn2Own competition at CanSecWest was again successful for French Vupen security, as they succeeded in exploiting Adobe Flash on Internet Explorer 9 on Windows 7 by chaining together three zero-days (an overflow, a ASLR bypass technique and a IE9 sandbox memory corruption) and earning themselves another $70,000.
George Hotz exploited Adobe Reader XI (also on IE 9 on Win7), and Ben Murphy - the last contestant to target Java - has also managed to earn a prize even though he wasn't there, because James Forshaw, a winner from the previous day, agreed to serve as proxy and demonstrate the attack.
All in all, ZDI has awarded over half a million dollars in cash prizes and, of course, the compromised laptops and ZDI reward points.
The Google financed Pwnium hacking contest - also held at CanSecWest - this year requires contestants to "break" Chrome OS but has so far not witnessed a successful exploitation.
In the meantime, Mozilla has already fixed the use-after-free zero-day flaw exploited yesterday by Vupen Security, and Google has issued a Chrome update that fixes the flaws discovered by the MWR Labs team.
Author: dfgdfg,
February 23, 2013
Windows 7 Commands Every Administrator Should Know
 PC troubleshooting is becoming less common in larger organizations, but consultants and techs in smaller shops still have to get their hands dirty identifying and fixing desktop problems. Oftentimes, troubleshooting Windows 7 means delving into the command line. Here are 10 fundamental Windows 7 commands you might find helpful.
PC troubleshooting is becoming less common in larger organizations, but consultants and techs in smaller shops still have to get their hands dirty identifying and fixing desktop problems. Oftentimes, troubleshooting Windows 7 means delving into the command line. Here are 10 fundamental Windows 7 commands you might find helpful.1: System File Checker
Malicious software will often attempt to replace core system files with modified versions in an effort to take control of the system. The System File Checker can be used to verify the integrity of the Windows system files. If any of the files are found to be missing or corrupt, they will be replaced. You can run the System File Checker by using this command:
sfc /scannow
2: File Signature Verification
One way to verify the integrity of a system is to make sure that all the system files are digitally signed. You can accomplish this with the File Signature Verification tool. This tool is launched from the command line but uses a GUI interface. It will tell you which system files are signed and which aren’t. As a rule, all the system files should be digitally signed, although some hardware vendors don’t sign driver files. The command used to launch the File Signature Verification tool is:
sigverif
3: Driverquery
Incorrect device drivers can lead to any number of system problems. If you want to see which drivers are installed on a Windows 7 system, you can do so by running the driverquery tool. This simple command-line tool provides information about each driver that is being used. The command is:
driverquery
If you need a bit more information, you can append the -v switch. Another option is to append the -si switch, which causes the tool to display signature information for the drivers. Here’s how they look:
driverquery -v
driverquery -si
4: Nslookup
The nslookup tool can help you to verify that DNS name resolution is working correctly. When you run nslookup against a host name, the tool will show you how the name was resolved, as well as which DNS server was used during the lookup. This tool can be extremely helpful when troubleshooting problems related to legacy DNS records that still exist but that are no longer correct.
To use this tool, just enter the nslookup command, followed by the name of the host you want to resolve. For example:
nslookup dc1.contoso.com
5: Ping
Ping is probably the simplest of all diagnostic commands. It’s used to verify basic TCP/IP connectivity to a network host. To use it, simply enter the command, followed by the name or IP address of the host you want to test. For example:
ping 192.168.1.1
Keep in mind that this command will work only if Internet Control Message Protocol (ICMP) traffic is allowed to pass between the two machines. If at any point a firewall is blocking ICMP traffic, the ping will fail.
6: Pathping
Ping does a good job of telling you whether two machines can communicate with one another over TCP/IP, but if a ping does fail, you won’t receive any information regarding the nature of the failure. This is where the pathping utility comes in.
Pathping is designed for environments in which one or more routers exist between hosts. It sends a series of packets to each router that’s in the path to the destination host in an effort to determine whether the router is performing slowly or dropping packets. At its simplest, the syntax for pathping is identical to that of the ping command (although there are some optional switches you can use). The command looks like this:
pathping 192.168.1.1
7: Ipconfig
The ipconfig command is used to view or modify a computer’s IP addresses. For example, if you wanted to view a Windows 7 system’s full IP configuration, you could use the following command:
ipconfig /all
Assuming that the system has acquired its IP address from a DHCP server, you can use the ipconfig command to release and then renew the IP address. Doing so involves using the following commands:
ipconfig /release
ipconfig /renew
Another handy thing you can do with ipconfig is flush the DNS resolver cache. This can be helpful when a system is resolving DNS addresses incorrectly. You can flush the DNS cache by using this command:
ipconfig /flushdns
8: Repair-bde
If a drive that is encrypted with BitLocker has problems, you can sometimes recover the data using a utility called repair-bde. To use this command, you will need a destination drive to which the recovered data can be written, as well as your BitLocker recovery key or recovery password. The basic syntax for this command is:
repair-bde
You must specify the source drive, the destination drive, and either the rk (recovery key) or the rp (recovery password) switch, along with the path to the recovery key or the recovery password. Here are two examples of how to use this utility:
repair-bde c: d: -rk e:\recovery.bek
repair-bde c: d: -rp 111111-111111-111111-111111-111111-111111
9: Tasklist
The tasklist command is designed to provide information about the tasks that are running on a Windows 7 system. At its most basic, you can enter the following command:
tasklist
The tasklist command has numerous optional switches, but there are a couple I want to mention. One is the -m switch, which causes tasklist to display all the DLL modules associated with a task. The other is the -svc switch, which lists the services that support each task. Here’s how they look:
tasklist -m
tasklist -svc
10: Taskkill
The taskkill command terminates a task, either by name (which is referred to as the image name) or by process ID. The syntax for this command is simple. You must follow the taskkill command with -pid (process ID) or -im (image name) and the name or process ID of the task that you want to terminate. Here are two examples of how this command works:
taskkill -pid 4104
taskkill -im iexplore.exe
Author: dfgdfg,
Turn Windows 8 PC into Wi-Fi Hot Spot
 In Windows 8, Microsoft quietly removed a useful networking feature: ad-hoc networks.
In Windows 8, Microsoft quietly removed a useful networking feature: ad-hoc networks.In Windows 7 (and previous OSes), the tool could turn your PC into a Wi-Fi hot spot, allowing it to share its Ethernet or other Internet connection with other devices by broadcasting its own network.
So, if you paid for Internet access at a cafe, or you're at work, and want to share your PC's Internet with your phone or tablet, this feature would let you do that.
It is very possible to do this in Windows 8, but the built-in method requires fiddling with the command prompt. And for some of us, walking into that black abyss is daunting.
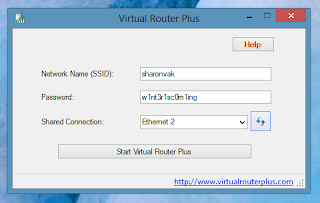
Instead, check out Virtual Router Plus. It's a free, open-source program that does the geek work for you, allowing you to quickly fire up an ad-hoc network whenever you need one.
Once you've downloaded the file, extract it, and launch the VirtualRouterPlus file within that folder. There's no real installation here -- the program will simply launch.
At this point, setup is easy. Enter a name for your network, then choose a secure password with at least eight characters. Finally, choose the connection you want to share (there will most likely only be one choice), and click Start.
To test it out, grab your phone or tablet and connect to your newly created Wi-Fi network. If it doesn't show up, stop the connection on your computer, and hit Start again.
Also remember that your computer needs to stay awake and running to keep its ad-hoc network alive. So, tweak your power settings if need be.
Author: dfgdfg,
LulzSec Hacker Sabu’s Sentencing Postponed
 The sentencing of Hector Xavier Monsegur – better known as Sabu, the leader of the infamous LulzSec hacker collective – has been postponed once again without any explanation.
The sentencing of Hector Xavier Monsegur – better known as Sabu, the leader of the infamous LulzSec hacker collective – has been postponed once again without any explanation.According to The Guardian, Monsegur was scheduled to appear at a Manhattan federal court on Friday where he should have been sentenced for 10 counts of hacking, one count of identity theft and one count of bank fraud.
This is not the first time when the hacker’s sentencing is postponed. Back in August, 2012, authorities requested a six-month adjournment because Sabu was still cooperating with the government.
Cooperation with the government is what made Monsegur become the symbol of treason among hacktivists. In March 2012, the alleged members of the LulzSec group were arrested after being ratted out by Sabu.
He was first arrested in June 2011, but the FBI released him in exchange for his assistance in apprehending other hackers.
Author: dfgdfg,
Pakistani Cyber Army Defaces 7 Indian Government Website
The affected websites are the ones of the Bihar Tourism from Ministry of Tourism India (bihartourism.gov.in), Mitigating Poverty in Western Rajasthan (mpowerraj.gov.in), the Directorate of Medical Education of the Government of Kerala (nurses.kerala.gov.in), the Salary Revision Commission of Government of Kerala (src.kerala.gov.in).
Other victims are the Customs, Excise & Service Tax Appellate Tribunal in New Delhi (cdrcestat.gov.in), the Works Information & Monitoring System (pwddelhi.gov.in) and the Society for Applied Microwave Electronics Engineering & Research (sameer.gov.in)
The hack comes in response to the attacks launched by Indian hackers against Pakistani websites. According to the deface message.
Here u g0 KiDs! Indian Government Servers Own3D! Hello GaY HinD People! Now Where’s SecuritY? ;) Listen U Fucked Up Indishell Kids! We Were Trying To Be in Peace! BuT We Don’t Think U Want It to Be Like That Anymore! So Here comes The Fuck From Us.At the time of writing, three of the websites were restored, two of them were still defaced, while the last two were taken offline altogether.
U abused All Pakistanis ( Which Includes Our Parents as Well )..I Had Told U AlreadY We have access to more than 50% of Indian GOV servers! BuT U ThoughT We MighT Be Kidding & U KepT Trying ur Lame ShiTs on .PK siTeS! When I see ur lame ShiTTy defaces on .PK SiTeS, It Drives me Real CrazY..Shame on U kids! :D
I Also Told U noT To Hack .PK Otherwise U will see Zone-h Full Of StarWhite Indian FLAG :D..Now Is The Time For Doing ThaT ShiT! In Other Words! We have Done this ShiT..
It appears the site’s administrators haven’t patched the vulnerabilities, since the sameer.gov.in has been defaced for the second time.
Author: dfgdfg,
February 19, 2013
Hacking Books for Serious Beginners Learning The Art of Hacking
Like I tell folks close to me, hacking involves so many things, and it requires an open minded individual with abundance of patience to succeed in this field, and believe when I say the road is not always pleasant. It's not always about using that point and click tool to ddos a web server or hijacking a user session or even installing backtrack thinking you've setup hacker's lab like any other
A hacker is a know all specie, an addicted reader with a logical frame of mind. I present this books that will help any motivated individual who is ready to explore the world of hacking.
The Basics of Hacking and Penetration Testing: Ethical Hacking and Penetration Testing Made Easy

The Basics of Hacking and Penetration Testing serves as an introduction to the steps required to complete a penetration test or perform an ethical hack. You learn how to properly utilize and interpret the results of modern day hacking tools; which are required to complete a penetration test. Tool coverage will include, Backtrack Linux, Google, Whois, Nmap, Nessus, Metasploit, Netcat, Netbus, and more. A simple and clean explanation of how to utilize these tools will allow you to gain a solid understanding of each of the four phases and prepare them to take on more in-depth texts and topics. This book includes the use of a single example (pen test target) all the way through the book which allows you to clearly see how the tools and phases relate.
Hacking: The Art of Exploitation, 2nd Edition

Hacking is the art of creative problem solving, whether that means finding an unconventional solution to a difficult problem or exploiting holes in sloppy programming. Many people call themselves hackers, but few have the strong technical foundation needed to really push the envelope.
Rather than merely showing how to run existing exploits, author Jon Erickson explains how arcane hacking techniques actually work. To share the art and science of hacking in a way that is accessible to everyone, Hacking: The Art of Exploitation, 2nd Edition introduces the fundamentals of C programming from a hacker's perspective.
The included LiveCD provides a complete Linux programming and debugging environment-all without modifying your current operating system. Use it to follow along with the book's examples as you fill gaps in your knowledge and explore hacking techniques on your own. Get your hands dirty debugging code, overflowing buffers, hijacking network communications, bypassing protections, exploiting cryptographic weaknesses, and perhaps even inventing new exploits.
Hackers are always pushing the boundaries, investigating the unknown, and evolving their art. Even if you don't already know how to program, Hacking: The Art of Exploitation, 2nd Edition will give you a complete picture of programming, machine architecture, network communications, and existing hacking techniques. Combine this knowledge with the included Linux environment, and all you need is your own creativity.
Hacking Exposed 7: Network Security Secrets & Solutions, Seventh Edition

The first version of Hacking Exposed came out in 1999. The book was a game changer that made penetration and vulnerability testing available to the masses. Needless to say that in the ensuing 13 years, there has been a huge amount of change in the world of information security.
With the release of Hacking Exposed 7: Network Security Secrets & Solutions, authors Stuart McClure, Joel Scambray and George Kurtz (along with over 10 contributing authors) provide an up to date version to the original classic. The book builds on the fundamentals of the first edition, and does include essentials of hacking on topics such as enumeration, foot printing, scanning, operating system detection and a lot more.
The latest edition gets into current threats and details the new menace of APT (advanced persistent threats), embedded hacking, database hacking, and significant coverage of mobile devices.
Bolster your system’s security and defeat the tools and tactics of cyber-criminals with expert advice and defense strategies from the world-renowned Hacking Exposed team. Case studies expose the hacker’s latest devious methods and illustrate field-tested remedies. Find out how to block infrastructure hacks, minimize advanced persistent threats, neutralize malicious code, secure web and database applications, and fortify UNIX networks. Hacking Exposed 7: Network Security Secrets & Solutions contains all-new visual maps and a comprehensive “countermeasures cookbook.”
Author: dfgdfg,



