January 30, 2012
Android Malware Now Exploits Steganography
Do you like this story?
Summary: Malware makers are turning to quite sophisticated tricks to disguise the true purpose of rogue applications.
Security firm F-Secure have released details on how Android malware makes use of steganography to hide the control parameters for rogue code.
First, what is steganography? It’s the technique of hiding messages within something else, in this case, an icon file.
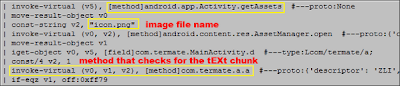
F-Secure first suspected that Android malware was making use of steganography when researchers came across this line of code:
Further digging revealed more code, and it soon became clear that the image file being referenced here was the icon file bundled with the rogue application:
So what’s this hidden information used for? It’s used to control how and when premium rate SMS messages are sent from the victim’s handset, which, as far as the bad guys are concerned, is the primary purpose of the rogue application.
You’ve got to admit, that’s a pretty clever use of steganography.
Security firm F-Secure have released details on how Android malware makes use of steganography to hide the control parameters for rogue code.
First, what is steganography? It’s the technique of hiding messages within something else, in this case, an icon file.
F-Secure first suspected that Android malware was making use of steganography when researchers came across this line of code:
Further digging revealed more code, and it soon became clear that the image file being referenced here was the icon file bundled with the rogue application:
So what’s this hidden information used for? It’s used to control how and when premium rate SMS messages are sent from the victim’s handset, which, as far as the bad guys are concerned, is the primary purpose of the rogue application.
You’ve got to admit, that’s a pretty clever use of steganography.
 About the Author:
Ifeanyi Emeka is the founder of this blog and also writes for Tech Forked. He is passionate about tech stuffs and loves customizing blogger themes.
About the Author:
Ifeanyi Emeka is the founder of this blog and also writes for Tech Forked. He is passionate about tech stuffs and loves customizing blogger themes.Popular This Week
Android Malware Now Exploits Steganography
2012-01-30T16:32:00Z
dfgdfg
Android|Android Malware|F-Secure|Malware|Steganography|
Subscribe to:
Post Comments (Atom)