June 16, 2011
LulzSec hackers claim breach of CIA website
Do you like this story?
The infamous rogue hacker group, Lulz Security, is back again with claims of packet-flooding the CIA’s Web site and leaking another lengthy list of email addresses and passwords.
CIA
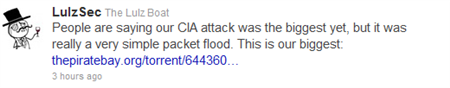
Following their recent exploits with the U.S. Senate website, LulzSec has now made the CIA their target via a packet-flooding attack. While it’s highly unlikely that the CIA’s Website has any sensitive data residing on it, the notion of such a high profile target being attacked is bad enough. To be fair, packet-flooding simply means they crashed the CIA’s server, but it can be a rather problematic issue to network health if certain precautions aren’t taken. The key takeaway here is the target of the attack. Per LulzSec’s Twitter feed:
In the second tweet, their proclamation of their most severe exploit at this point is the release of internal information from Bethesda Software. The release included server admin configurations, admin staff and blog user hashes, server logs, and mappings of Arkane, Bethblog, Brink codes, Brink signups, IDSoftware, Rage, and more.
While far more data was released with the Bethesda attack, the reason the CIA attack is considered their biggest is because of who it is, thus the potential repercussions.
Emails and Passwords
The last LulzSec-released list of email addresses and passwords totaled 26,000, and they were all obtained via hacked pornographic sites. This time, they’re keeping quiet about the sources of this latest list of culminated addresses. Regardless of the sources, here are 62,000+ email addresses and passwords just released. From their Twitter feed:
Many users have taken to Twitter to let LulzSec know either how they have been attacked due to the leaked list, or how they have benefited by exploiting the leaked information. Make no mistake, LulzSec is essentially releasing this information into the hands of people with malicious intentions.
As with before, it is highly advised that you download the list and check for your email address so as to change your password. You can obtain the leaked list here (visit the link to download the file). Use the “find/search” functionality of your browser/text viewer to search for your email address once you download the 2.25 MB text file.
While neither of these latest activities were posted to LulzSec’s blog as official releases, it’s clear that they intend on utilizing any and every avenue they can to show off their exploits.
Lastly, while the image of a small group of individuals comes to mind in regards to the make-up of LulzSec, there is increasing speculation that the group — along with the equally-notorious rogue hacker group, Anonymous — is actually comprised of many people; possibly thousands. If true, this makes the efforts of these groups much more difficult to stop. However, as entities like the CIA and the U.S. Senate are targets of these groups, we may all soon find out just what the make of these groups really is.
How do you feel about LulzSec’s latest actions? Share your thoughts in the comments below!
CIA
Following their recent exploits with the U.S. Senate website, LulzSec has now made the CIA their target via a packet-flooding attack. While it’s highly unlikely that the CIA’s Website has any sensitive data residing on it, the notion of such a high profile target being attacked is bad enough. To be fair, packet-flooding simply means they crashed the CIA’s server, but it can be a rather problematic issue to network health if certain precautions aren’t taken. The key takeaway here is the target of the attack. Per LulzSec’s Twitter feed:
LulzSec Target CIA
LulzSec says they packet-flooded the CIA
In the second tweet, their proclamation of their most severe exploit at this point is the release of internal information from Bethesda Software. The release included server admin configurations, admin staff and blog user hashes, server logs, and mappings of Arkane, Bethblog, Brink codes, Brink signups, IDSoftware, Rage, and more.
While far more data was released with the Bethesda attack, the reason the CIA attack is considered their biggest is because of who it is, thus the potential repercussions.
Emails and Passwords
The last LulzSec-released list of email addresses and passwords totaled 26,000, and they were all obtained via hacked pornographic sites. This time, they’re keeping quiet about the sources of this latest list of culminated addresses. Regardless of the sources, here are 62,000+ email addresses and passwords just released. From their Twitter feed:
LulzSec releases 62,000 emails/passwords
Many users have taken to Twitter to let LulzSec know either how they have been attacked due to the leaked list, or how they have benefited by exploiting the leaked information. Make no mistake, LulzSec is essentially releasing this information into the hands of people with malicious intentions.
As with before, it is highly advised that you download the list and check for your email address so as to change your password. You can obtain the leaked list here (visit the link to download the file). Use the “find/search” functionality of your browser/text viewer to search for your email address once you download the 2.25 MB text file.
While neither of these latest activities were posted to LulzSec’s blog as official releases, it’s clear that they intend on utilizing any and every avenue they can to show off their exploits.
Lastly, while the image of a small group of individuals comes to mind in regards to the make-up of LulzSec, there is increasing speculation that the group — along with the equally-notorious rogue hacker group, Anonymous — is actually comprised of many people; possibly thousands. If true, this makes the efforts of these groups much more difficult to stop. However, as entities like the CIA and the U.S. Senate are targets of these groups, we may all soon find out just what the make of these groups really is.
How do you feel about LulzSec’s latest actions? Share your thoughts in the comments below!
 About the Author:
Ifeanyi Emeka is the founder of this blog and also writes for Tech Forked. He is passionate about tech stuffs and loves customizing blogger themes.
About the Author:
Ifeanyi Emeka is the founder of this blog and also writes for Tech Forked. He is passionate about tech stuffs and loves customizing blogger themes.Popular This Week
LulzSec hackers claim breach of CIA website
2011-06-16T21:23:00+01:00
dfgdfg
CIA|Hacking|LulSec|Lulz Security|LulzSec Hackers|Tech News|
Subscribe to:
Post Comments (Atom)