May 17, 2011
pytbull – Intrusion Detection/Prevention System (IDS/IPS) Testing Framework
Do you like this story?
pytbull is an Intrusion Detection/Prevention System (IDS/IPS) Testing Framework for Snort, Suricata and any IDS/IPS that generates an alert file. It can be used to test the detection and blocking capabilities of an IDS/IPS, to compare IDS/IPS, to compare configuration modifications and to check/validate configurations.
The framework is shipped with about 300 tests grouped in 9 testing modules:
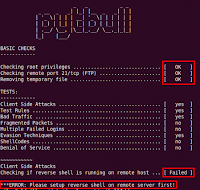
There are basically 6 types of tests:
Changes/Improvements in V1.1
pytbull-1.1.tar.bz2
Or read more here.
The framework is shipped with about 300 tests grouped in 9 testing modules:
- clientSideAttacks: this module uses a reverse shell to provide the server with instructions to download remote malicious files. This module tests the ability of the IDS/IPS to protect against client-side attacks.
- testRules: basic rules testing. These attacks are supposed to be detected by the rules sets shipped with the IDS/IPS.
- badTraffic: Non RFC compliant packets are sent to the server to test how packets are processed.
- fragmentedPackets: various fragmented payloads are sent to server to test its ability to recompose them and detect the attacks.
- multipleFailedLogins: tests the ability of the server to track multiple failed logins (e.g. FTP). Makes use of custom rules on Snort and Suricata.
- evasionTechniques: various evasion techniques are used to check if the IDS/IPS can detect them.
- shellCodes: send various shellcodes to the server on port 21/tcp to test the ability of the server to detect/reject shellcodes.
- denialOfService: tests the ability of the IDS/IPS to protect against DoS attempts
- pcapReplay: enables to replay pcap files
There are basically 6 types of tests:
- socket: open a socket on a given port and send the payloads to the remote target on that port.
- command: send command to the remote target with the subprocess.call() python function.
- scapy: send special crafted payloads based on the Scapy syntax
- multiple failed logins: open a socket on port 21/tcp (FTP) and attempt to login 5 times with bad credentials.
- client side attacks: use a reverse shell on the remote target and send commands to it to make them processed by the server (typically wget commands).
- pcap replay: enables to replay traffic based on pcap files
Changes/Improvements in V1.1
- Issue #2 fixed (test number incrementing twice just after the last test from multipleFailedLogins test)
- Issue #3 fixed (pcapReplay module not present in the checks on STDOUT)
- Code factoring in pytbull.py
- Timing options are now in parameters (config.cfg)
- Automatically checks and informs if a new version is available (use PROXY section in the configuration file if needed)
- New basic checks: Checks that paths are valid
- SVN tags added in source code
pytbull-1.1.tar.bz2
Or read more here.
 About the Author:
Ifeanyi Emeka is the founder of this blog and also writes for Tech Forked. He is passionate about tech stuffs and loves customizing blogger themes.
About the Author:
Ifeanyi Emeka is the founder of this blog and also writes for Tech Forked. He is passionate about tech stuffs and loves customizing blogger themes.Popular This Week
pytbull – Intrusion Detection/Prevention System (IDS/IPS) Testing Framework
2011-05-17T16:41:00+01:00
dfgdfg
Hacking Tricks|pytbull|pytbull intrusion|Remote file Intr|
Subscribe to:
Post Comments (Atom)